Introduction
Sensitive information for Java applications is commonly placed in XML file context.xml/server.xml, which is required by web application at runtime. This config file has sensitive information for making connection to databases or SMTP server, API keys used within the application or for connecting internal/external web services. This sensitive information like database name, port, username, and password/other information has to be encrypted from being exposed to everyone.
In case of using Apache Tomcat webserver, Tomcat’s JNDI connections are defined within XML configuration files server.xml or context.xml within either Tomcat’s global configuration or within the deployed web application. Tomcat’s use of XML for connection definition potentially exposes the password for these connections as plain text. While these files should be on a server where access to these configuration files is secured and monitored, passwords in plain text may be a challenge for all environments.
Apache Configuration Container
Apache Tomcat Servlet/JSP container’s connection pull configuration via JNDI (Java Naming and Directory Interface ) resources. The connection pool we will look at is javax.sql.DataSource, which is a JDBC API for getting a connection instance to a database.
javax.sql.DataSource is a factory for getting connections to different physical data sources. javax.sql.DataSource interface is registered with the naming service based on JNDI API. A data source driver allows accessed to the database via DataSource interface. A DataSource object is looked up in the context based on registered through JNDI Resource. The connection to the data source, such as database is attempted when javax.sql.DataSource‘s getConnection() method is called.
JDBC API acts as an interface between Java applications and database systems allowing the same Java code base to be used with different database systems.
To encrypt passwords in context.xml we will need to create custom factory based on AES encryption and specify the factory in context.xml.
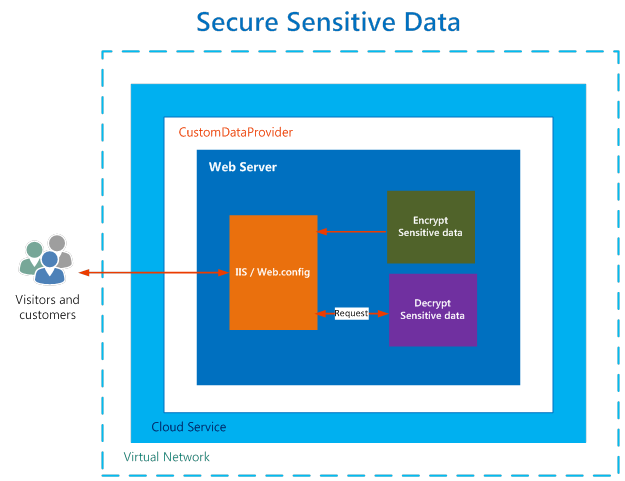
Architecture to Encrypt password using custom factory
We will create a custom factory based on Advanced Encryption Standard(AES) encryption algorithm, which will encrypt any sensitive information stored in Context.xml. Apache Tomcat at runtime is cable of decrypting the sensitive information stored in Context.xml with custom factory to run web applications.
Below shows the complete process of encryption and decryption of Context.xml.
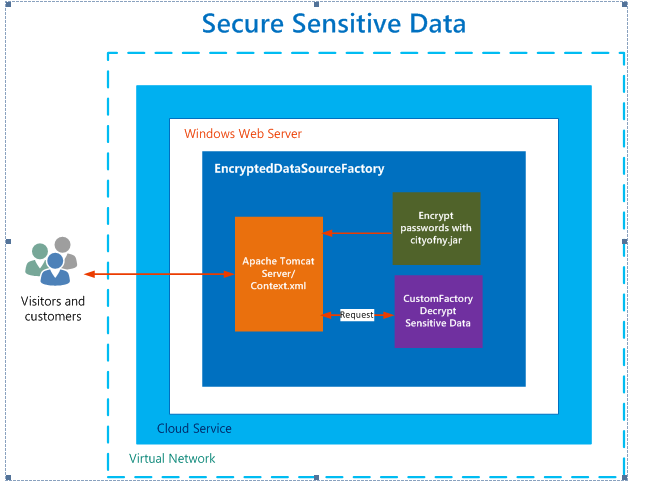
Create Custom Data source Factory & Encrypt File
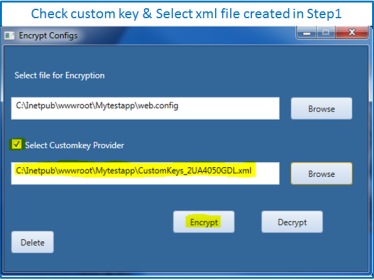
Here are the steps to encrypt Context.xml file.
-
Simple config file <Context> <Resource auth="Container" driverClassName="com.microsoft.sqlserver.jdbc.SQLServerDriver" maxActive="100" maxIdle="10" minEvictableIdleTimeMillis="60000" maxWait="-1" name="DBDataSource" password="keepitsecret26" type="javax.sql.DataSource" poolPreparedStatements="true" maxOpenPreparedStatements="100" url="jdbc:sqlserver://nycr-dmzsqlserver:2433;databaseName=SENSITIVEPRODDB; integratedSecurity=true" username="whatsupuser" validationQuery="SELECT 1"/> </Context>
- Create custom encryption factory using AES encryption.
- Create/generate cityofny.jar from step2. or download from here
- Generate new encrypted password using custom data source factory from step3.
- Append Context.xml file with Custom Data Source Factory and update password with encrypted value.
<Context> <Resource auth="Container" factory="com.secure.hroit.EncryptedDataSourceFactory" driverClassName="com.microsoft.sqlserver.jdbc.SQLServerDriver" maxActive="100" maxIdle="10" minEvictableIdleTimeMillis="60000" maxWait="-1" name="DBDataSource" password="c24d8b7c07fe2bb07e4941912968baaf00e60f8170bc365ea06a428afe6a558" type="javax.sql.DataSource" poolPreparedStatements="true" maxOpenPreparedStatements="100" url="jdbc:sqlserver://nycr-dmzsqlserver:2433; databaseName=SENSITIVEPRODDB;integratedSecurity=true" username="whatsupuser" validationQuery="SELECT 1" /> </Context>
Steps to Encrypt Context.xml file
Jar file is available for download from here.
1. Copy the cityofny.jar to this Tomcat instalation diretory. For example C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib.
- Run below java command to get encrypted password using jar created above.
For example, C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib>java -jar newyorkcity.jar mysecretpassword
- Above command will output the password similar to this.
mysecretpassword: c24d8b7c07fe2bb07e4941912968baaf00e60f8170bc365ea06a428afe6a558
- Copy the password and replace it in Context.xml file in Tomcat. Restart Tomcat webserver for changes to take effect.
References:
http://www.jdev.it/encrypting-passwords-in-tomcat/